This setup attempts to configure a network where one subnet (192.168.2.x) uses a VPN connection as its default route where as another subnet (192.168.1.x) has a default route to the internet. The devices on each subnet should be able to see each other and communicate, this might be used for e.g. Apple TV (see).
Here is an overview of how the system could look like:
Network Description
- Modem: 10.10.10.1/255.255.255.0
- R1: Gateway
- WAN: 10.10.10.1/255.255.255.0
- LAN: 192.168.1.1/255.255.255.0
- R2: VPN Router
- WAN: 192.168.1.100/255.255.255.0
- LAN: 192.168.2.1/255.255.255.0
Configuration of R2: VPN Router
This router cannot use the default DD-WRT setup but needs to be configures as a “router” and not a gateway, because we don’t want NAT. We want to provide direct access between R1 and R2:
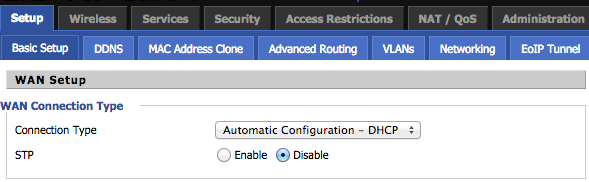
Configure the WAN side to obtain an ip from R1, we will declare this as a static entry such that it always gets the same ip (in R1):
The router mode must be changed in R2:
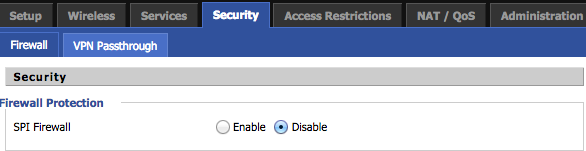
And finally we need to disable SPI Firewall to allow direct connection from R1 to R2:
To allow traffic form R2 to access the R1 network we need to add a route for it, but before we can do so we need to clarify which interface refers to which physical connection:
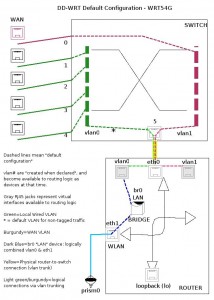 We can see from the schematic of the WRT54GL which is used here that:
We can see from the schematic of the WRT54GL which is used here that:
- vlan0 is the local LAN
- vlan1 is WAN
- bro is the local LAN + WLAN
We then use this to add a route from 192.168.2.x to 192.168.1.x devices:
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.1.0 * 255.255.255.0 U 0 0 0 vlan1 default Rl 0.0.0.0 UG 0 0 0 vlan1
I stripped the other entries from route.
The command for adding are:
route add -net 192.168.1.0 gw 192.168.1.1 netmask 255.255.255.0 dev vlan1 route add default gw 192.168.1.1 netmask 255.255.255.0 dev vlan1
The VPN connection can be made using standard OpenVPN configuration like provided by Hide My Ass.
Configuration of R1: Gateway
The gateway may just use a default DD-WRT gateway configuration where it obtains an WAN ip through DHCP or whatever is required by the ISP.
The static ip of R2 can be configures under: Services->Services:
To make the 192.168.2.x network accessible from R1 a route to R2 must be added to the routing table (on this device eth1 is the WAN port and br0 is like above):
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.2.0 R2 255.255.255.0 UG 0 0 0 br0 default Modem 0.0.0.0 UG 0 0 0 eth1
The commands are:
route add -net 192.168.2.0 gw 192.168.1.100 netmask 255.255.255.0 dev br0
If any other known ip should be routed through the VPN when accessed from R1 clients then it should just be added here, since the default route of R2 would be configures to use the VPN connection once installed on R2.
VPN Connection:
A script is avaliable from e.g. Hide My Ass here but in case you have an account with them you can just login and get a command to place in the command box in the router to install it.
However, to detect if the public ip actually switched this shell script command can be used:
wget -qO- http://ipecho.net/plain ; echo



Leave a Reply